You’ve seen the steady stream of headlines reporting massive data breaches. Now let’s go inside the concept of a data breach to see what’s really going on.
A data breach is a security event where highly sensitive, confidential or protected information is accessed or disclosed without permission or is lost. Organizations, governments and individuals can be victims of data breaches, and usually these events are enormously costly in terms of time, money or corporate reputation.
To give you an idea of the size and scale of some data breaches, 3.5 billion people had records exposed in the 15 biggest data breaches of this century. In just the first half of 2019, data breaches exposed 4.1 billion records.
What causes data breaches?
Data breaches can occur in four different ways:
- Someone inside an organization inadvertently accesses and views information.
- Someone inside an organization purposefully accesses and/or shares information with malicious intent.
- Devices containing sensitive information are stolen or lost.
- Criminals use a range of increasingly sophisticated means such as phishing emails, brute force attacks and malware to exploit weaknesses in networks or individual behavior, for profit, reputation or disruption (or all three). Read the top 5 security concerns this year.
According to the Verizon 2020 Data Breach Investigations Report that analyzed 32,002 security incidents, of which 3,950 were confirmed breaches:
- 70% of data breaches in the reporting period were perpetrated by external actors.
- 45% of breaches featured an intentional effort to subvert a system’s security.
- 22% of breaches were caused by errors.
- Money motivated 86% of all breaches in the reporting period.
- Credential theft, social attacks (e.g. phishing and business email compromise) and errors caused most breaches (67% or more).
As of 2019, the World Economic Forum put cyberattacks in the top five risks to global stability. Worldwide, more than 80% of cyberattacks come from phishing emails, which deliver 94% of malware. In the first six months of 2019, attacks on Internet of Things devices (one of the fastest-growing emerging technologies) tripled, and malware attacks that leverage applications already installed on a system (known as fileless attacks) increased by 256%.
How does a criminal carry out a data breach?
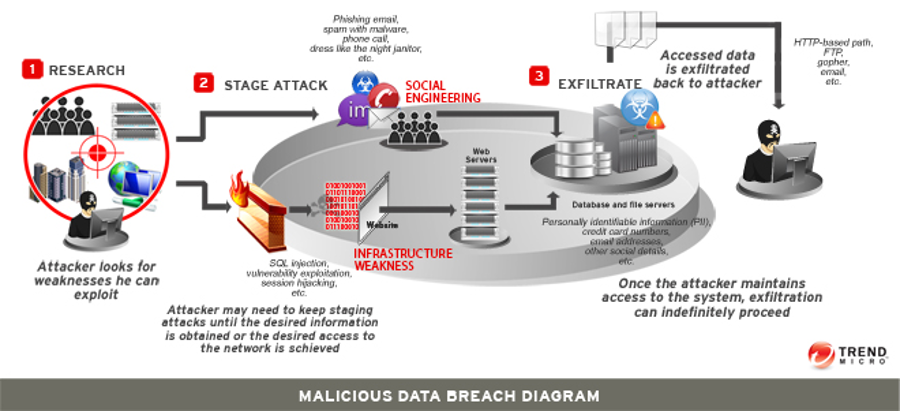
A criminally motivated data breach typically goes like this:
- Research the target’s security (people, systems, or networks) and identify weaknesses.
- Attack the target using either a network attack (attacking the infrastructure, systems or applications of an organization, as above) or a social attack (tricking employees into giving up corporate login credentials or downloading malicious malware or ransomware).
- Extract the confidential data and exfiltrate the network.
What can be exposed in a data breach?
Data breaches expose highly sensitive personally identifiable information or PII. PII isn’t only email and passwords; it’s any data that can be used to identify a person, including name, SSN, passport number, driver’s license number, credit card details, residential addresses, telephone numbers, and photographic images, x-rays, and fingerprints. Here are more examples of sensitive personal data.
What are the motivations behind a data breach?
Often, criminals will steal data on behalf of a third party or sell it on the dark web. The information is used for other crimes such as identity theft (e.g. creating fake passports) and credit card and other financial fraud (e.g. applying for loans in the victim’s name). Some criminals demand a ransom from the victim, and often they’re seeking acclaim within the criminal community and/or disruption to critical infrastructure, particularly in the case of healthcare and government data breaches.
Unfortunately, most often the target is unaware the data was stolen until it’s too late to do anything about it. Onaverage, data breaches take five months to detect so there is plenty of time for damage to be done.
How do you know if you’ve been caught in a data breach?
The affected organization(s) should advise you of the breach event, but many individuals find out secondhand from the media for data breaches involving well-known companies. Some online services allow you to track your digital footprint so you will be notified when your personal data is part of data breach or is being misused.
CSO Online lists these 15 signs that you’ve been compromised:
- You get a ransomware message.
- You get a fake antivirus message.
- You have unwanted browser toolbars.
- Your internet searches are redirected.
- You see frequent, random popups.
- Your friends receive social media invitations from you that you didn’t send.
- Your online password isn’t working.
- You observe unexpected software installs.
- Your mouse moves between programs and makes selections.
- Anti-malware, Task Manager or Registry Editor is disabled.
- Your online account is missing money.
- Someone notifies you to say you’ve been hacked.
- Confidential data has been leaked.
- Your credentials are in a password dump.
- You observe strange network traffic patterns.
Here are more ways to tell if you have a compromised account. If any of this is true for you, head to our article: What Should I Do If I’ve Been Caught In a Data Breach?
Use MySudo to guard against data breaches
To avoid being caught up in a data breach, you need to break the data trails or digital exhaust that you leave behind every time you interact online. This means you stop using your personal information, such as email address and phone number, to sign up, download and buy online, and instead use Sudo profiles in MySudo, the world’s only all-in-one privacy app.
A Sudo is a secure, customizable digital identity or ‘profile’ that intentionally differentiates from your personal identity and protects your personal data. You assign each of your Sudos (you can have up to nine in the app) a real working phone number, email, and virtual card for online purchases, plus you get a dedicated private browser for searching completely ad and tracker free.
You give each of your Sudo profiles a purpose, like shopping online, selling second-hand goods, or booking local services. Then every time you talk, text, email or pay in a particular context such as online shopping, you use your Sudo profile information instead of your personal information. Your own personal details are secure since you haven’t shared them—we won’t even ask for a username or password to set up the app.
MySudo allows you to search the internet without ads and pop-ups using the private browser; pay online with your virtual card without worrying about tracking or fraud; call, text, and email anyone without giving up your private details; and get end-to-end encrypted talk, text and email with other MySudo users.
Put simply, MySudo means you stop putting your personal data at risk of data breach—a powerful, proactive step you can take today. Discover more on our blog, or download MySudo for iOS or Android.
Photo by Clint Patterson on Unsplash